These experts know how to take benefit of every loophole in the system to break into your system and steal data or use it as a spur for further attacks. To stay protected from these stylish attackers and reduce the risk of becoming a target, Guest Posting you need to realize multiple security measures, you can do that by hire a Cyber Security Company. After all, there’s no single solution that can tackle every single cyber danger; rather, there are different strategy that work in combination with each other to reduce the attack surface while concurrently defensive your association next to vulnerabilities. That being said, we’ve outline some of the best practices you can adopt to keep your Windows-based network secure from cyber threats
Change the default passwords

As tempting as it may be to use the same password for manifold accounts and application, it’s not a good idea. As the maxim goes, “if Wall Street bankers can’t get it right, then why should we be any less careful?” That is, if you want to keep your in order and network safe from cyber threats, you have to apply the same caution to your own security practices. When it comes to passwords, you shouldn’t make the mistake of using simple words and phrase out of context. Instead, use a Technology password made up of a combination of letters, numbers, and symbols a secure password. Make sure you change the default passwords of your application and accounts to something more secure.
Educate your employees on risks and safety precautions

For most people, the idea of custody their workplace safe from cyber threats doesn’t seem like much of a priority. But when an assailant successfully breaches a system, the damage he can cause is vast. In fact, the standard cost of a data breach is $3.95 million. To Technology prevent this from occurrence, you need to teach your employees about the safety defense they need to take. For example, you can have your employees frequently change their passwords. You can also have them use two-factor verification whenever possible, such as when classification in from a new device or computer. Also, you can also have them regularly scan their processor for potential security risks, like malware or spyware.
Encryption is the key
Encryption is the most vital security tool you can use on your Windows network. It’s a process that transforms data into an unreadable format and is therefore almost illegible. The problem is that not all encryption programs are created equally. Some may be easy to break while others are so higher that even a well-funded cyber criminal team would need to work for months to crack them. Furthermore, if one of your employees is fixed using an unsecured device, he may also be able to access any data stored on the device or even on the network. To find the best encryption program for your association, consult a third-party safety review website, like ours. It may help you choose the right program for your needs.
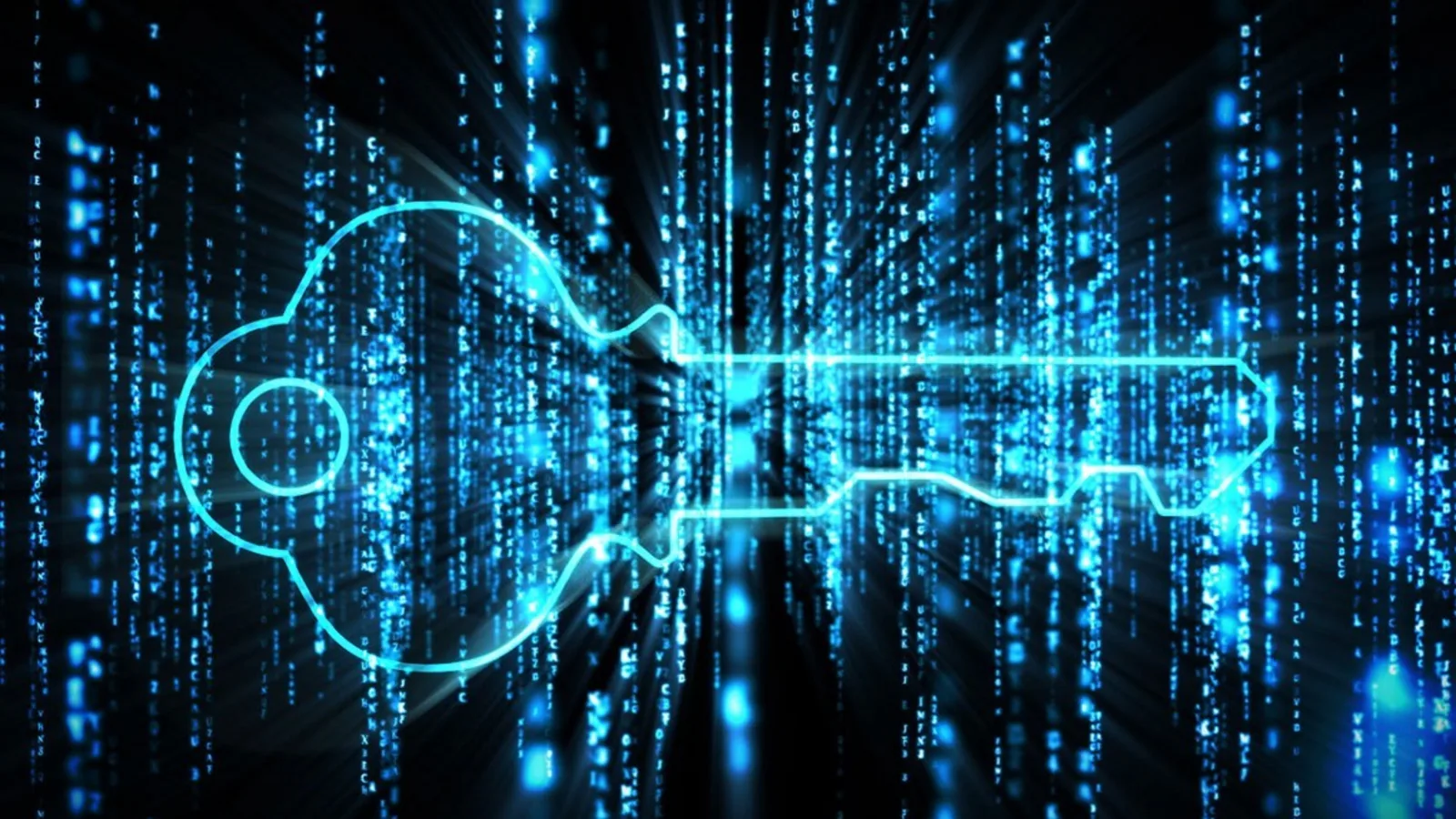
Keep Windows Up to Date
Custody your Windows software up to date is essential to ensure the security of your network. As new patch are released, researchers generally find and fix a number of vulnerabilities on Windows operating system. But because these vulnerabilities generally go ignored until a hacker finds them and uses them to break into a network, update your Technology software is crucial to staying secluded. You can easily determine whether your Windows computer is up to date by gap the setting app, select the System icon in the left pane, and then looking at the “Updates” section. Make sure that your computer indicate that it’s up to date.
Limit which users have access to your network

Cyber criminals are always on the lookout for networks that they can penetrate and use as springboard for further attacks. And while some network is more likely to be attacked than others, they all share one common trait: they’re linked to the Internet. So, before you grant Internet Technology access to your network to your workers or clients, think about which ones you want to grant access to and for how long. For example, grant distant access for a set amount of time, like a week at a time, and then revoke it. This will make it harder for an attacker to gain access to your network.
Implement Strong User Authentication m clever your network and stealing data, you need to apply strong user authentication, like two-factor verification. It comes as no surprise, then, that it’s one of the first Technology security measures you can apply on your Windows network. Two-factor confirmation is a security measure that requires a user to have two forms of verification, like something they have, like a phone, or something they’re, like a password, in order to log in to an account.
m clever your network and stealing data, you need to apply strong user authentication, like two-factor verification. It comes as no surprise, then, that it’s one of the first Technology security measures you can apply on your Windows network. Two-factor confirmation is a security measure that requires a user to have two forms of verification, like something they have, like a phone, or something they’re, like a password, in order to log in to an account.
Defend with Network Tools and Other Software

To effectively protect your Windows-based network, you need to make sure that your devices are as secure as possible. To do this, you can use an wide Security feature on Windows 10 or enable hardware-based security on your computer. You can also use network tools and other software to protect your network.
Penetration Testing Can Help

A pen-test is a type of security taxing that focuses on the completion, pattern, and operation of a system. The Pen test program used to test the security of a system next to various types of attacks such as application-level attacks, network-level attacks, and protocol-level attack. A pen-test is often carried out by an ethical hacker or certified penetration tester who uses their skills and facts to test the safety of a system.
The main goals of diffusion testing are to recognize vulnerabilities in the Technology system and to determine the best ways to improve security. By conduct a thorough Penetration taxing, an club not only can minimize the window-based attacks on their networks but also can identify vulnerabilities to can lead to financial losses. In adding, organization should keep track of all access needs. This will help them to know who is access their network and how they are doing it.
Patching
Finally, it’s vital to keep in mind that even when you do all right, there’s a chance that your network will still compromised. And to Technology have any chance of thwarting an attack, you have to patch your systems as soon as possible. while it comes to patching, every system is diverse. Some are more likely to be attack than others, and some are more likely to overlooked than others. That’s why it’s important to know which systems on your network are the most likely to be attack. To find out which systems are most likely to attacked, use a request, like Network Mapped, to map out your network. You can also use a tool, like Microsoft’s, to identify which systems need to patched. Make sure to update your systems as soon as possible to protect next to the latest threats. These are just some of the best practice you can apply to keep your Windows-based network secure from cyber threats.